The purpose of this CXTech Week 4 2024 newsletter is to highlight, with commentary, some of the news stories in CXTech this week. What is CXTech? The C stands for Connectivity, Communications, Collaboration, Conversation, Customer; X for Experience because that’s what matters; and Tech because the focus is enablers.
You can sign up here to receive the CXTech News and Analysis by email or by my Substack. Please forward this on if you think someone should join the list. And please let me know any CXTech news I should include.
Covered this week:
- Was the FCC Lied to? What the FCC was told on SMS spam.
- Podcast 27: Truth In Telecoms. Taking Back Control & Save Grandma – The Fight Against SMS Spam and Robocalls!
- Podcast 26: TADSummit Innovators, Steven Goodwin
- Remembering TADHack-mini Phoenix 2020, sponsored by Avaya with partners Google and GitHub.
- Truly Awful CPaaS Landscapes
- Juniper Research highlights $3B loss SMS Business Messaging
- US SEC set to require more transparency from SPACs
- Real-time HLR Scam
- People, Gossip, and Frivolous Stuff
Was the FCC Lied to? What the FCC was told on SMS spam.
I was reviewing the replies to FCC’s Targeting and Eliminating Unlawful Text Messages, CG Docket No. 21-402 published in 2022. You can see all of the replies here. Some that drew my attention are listed below.
The Campaign Registry (TCR) Reply.
Before we begin:
The FCC document is about “Targeting and Eliminating Unlawful Text Messages.” However, TCR claims to store business data and never claims to stop spam or robo-texting. It does not target or eliminate any unwanted text messages. Its role is a commercial entity that charges fees for vetting campaigns, and according to TCR insiders at Tata Communications’ direction TCR must increase profits every quarter.
Nothing is actually blocked or stopped by TCR. The “registered” status only serves as a flag to allow a message to pass without further scrutiny, whether it is good or bad, and to allow CSPs/DCAs (Campaign Service Provider / Direct Connect (to telco/carrier) Aggregator) to receive lower termination fees from the carriers.
Specifics in the TCR text:
Page 3. “enable our stakeholders to track messaging back to its origins so that they can conduct the necessary follow up for the messaging in question”
The tracking of authorizations and a brand’s identity remains a challenge for TCR. It stems from TCRs dependance on those who register campaigns as the supplier of identity. A spammer could register your well-established business with TCR, sign up for service with a voice telephone company for telephone numbers, text enable them with another company, and the send out scams, fraud, phishing. They only need a few minutes of phishing or hours of spamming to generate a good return on their investment. As most of the work is done through APIs, it can be highly automated.
Another challenge is TCR does not track any of the phone numbers. It uses an API to check registered campaign numbers in NetNumber’s database. NetNumber supposedly has provided a sync to its number history; this tool is ONLY available to carriers and tier 1 DCA (Syniverse and Sinch).
Netnumber’s inability to allow its customers to control their authorizations and or digital rights, continues to harm the ecosystem. Cross-company identity management fails to protect and track identity and / or authorizations attached to telephone numbers. This aids spammers and delays the time for action to be taken in closing off numbers that are spamming / phishing.
Only the currently active registered 10DLC campaign ID is available from NetNumber. When a 10DLC is unregistered from a campaign by the DCA, there is no trace of that 10DLC being associated with any campaign. The TCR has no memory and depends on the other messaging monopolies to keep their records straight.
Netnumber has had some security and operational issues with number management. We covered the hack here, interviewing the hacker Lucky225. They were socially engineered by a white hat hacker, and let numbers get ported without direct authority and they have no way to digitally track and attest the ownership rights are accurate.
This setup only provides the MNO with an ability to check bad messages one-by-one. Assuming that the text was sent from a registered number in the first place and further assuming that the number is still registered. This setup does nothing for any unregistered traffic.
A broader issue is carriers have the ability to block messages, they could simply block any spam they detect, without all the messaging monopolies. It would seem the easiest fix to this problem, and according to some brands this appears to be happening on some of their campaigns.
CSPs are reporting the carriers are suspending campaigns that went through the lengthy TCR process, vetted and approved by multiple parties. Let’s say days to approve and seconds to shut it down. However, the carriers are not shutting down spam being generated from their networks and SIMs, which is often P2P.
<There are lots more specifics in the post>
Twilio Reply
This is an example of a response from the messaging insiders. “SMS spam controls are working, we can work together to make them even better.”
Self regulation is usually a way to pass the buck to the future, and rarely solves the problem for the end customer.
Given the challenges we’ve seen with 800SMS / Toll Free SMS in the past week, many CSPs and brands are suffering in the name of SMS spam control. Yet, Nikki keeps texting me!
Cloud Communications Alliance Reply
Lists the real world problems with the current SMS industry solutions, and calls for an identity based solution. The common ground with the industry insiders in STIR/SHAKEN is not the answer.
Check out the Telecom Triopoly analysis and the squeeze being put on the UCaaS (Unified Communications as a Service) providers, who are CCA’s members.
Current Status
Last month the FCC released several new rules on SMS spam, as discussed in CXTech Week 50 newsletter.
Taking a step back to the comments on the FCC’s CG Docket No. 21-402, the messaging industry said we do not need STIR/SHAKEN we can sort this out ourselves. It’s clear they can not.
The FCC is now applying band-aids that are within their control (telecoms) in a knee-jerk reaction, which has the brands and CSPs up in arms.
We’ve discussed on the blog the importance of identity (copying cyber security rather than the current ineffective process from George Orwell’s 1984), and AI (working at scale) are critical technologies for adequate SMS spam control.
A tiger team must be assembled that is NOT dominated by the messaging monopolies, rather proven technology experts from across telecoms and cyber security (Internet), who can fast-track an adequate solution. This is a soluble problem, it’s simply a matter of motivation to innovate.
An approach could be to empower the consumer with self-managed identity. To set their own data privacy terms and documented consent. One that the FCC could then enforce rights and rules to the carrier as they have done with interoperability in the past.

Podcast 27: Truth In Telecoms. Taking Back Control & Save Grandma – The Fight Against SMS Spam and Robocalls!
A short podcast this week, a video from TNID, “Taking Back Control & Save Grandma – The Fight Against Spam and Robocalls!”
Its a call to action for all of us to fight against Robocalls and SMS spam.
To do this click the link below to tell the FCC your robocalling / SMS spam horror stories! www.fcc.gov/ecfs/filings/express
Use 02-278 in the proceeding filed and the rest is pretty easy.
Share your experiences on how Robocalls and SMS Spam have affected your family and/or business in the “Brief Comment” section.
Check out the TNID Handout for this video.
Podcast 26: TADSummit Innovators, Steven Goodwin
Steven Goodwin has been part of TADHack since 2015, attending the Lisbon location, and creating the hack, Note to Self.
He’s a developer, author (20 Goto 10), Magician, AI musician, keynote speaker, and FOSDEM regular.
When I first met Steven in 2015 he was working on a remote learning start-up, 3rd Space Learning. This was way before its time given the pandemic. The focus is helping improve access to math tutors.
Over the years Steven has created many hacks, and as importantly helped TADHack sponsors and other hackers achieve more through their involvement in TADHack.
During the pandemic Steven with his partner Lily created 3 hacks over one event! Not one has yet matched this feat.
- Wizard Chess by Lily Madar and Steven Goodwin. Play chess with your voice, making it accessible for those with visual impairments or less able motor skills. The code is a basic Node app, running on a server which starts by making a Telnyx call to the conference room, which symbl.ai then joins. From there, anything said into the phone is processed by symbl.ai and passed via websockets to the web page. Computer moves are relayed by voice in the opposite direction to only the human player.
- Colloqui11ly by Lily Madar and Steven Goodwin. ccessible conferencing solution (using TTS and STT). It makes the conference available to all by allowing some users to interact via text message (both to “hear” the chat, and respond) while others get the audio experience.
- Podcast Annotator by Lily Madar and Steven Goodwin. Hands-free note-taking while listening to a podcast stream. You first start a podcast from the webpage, which initiates a call to your phone. (But it could also be triggered by DTMF tones.) At this point you can listen to the podcast, and say things like “Good point” and “must look that up”. These phrases are transcribed and added to a timeline for later review. Once the podcast ends, this review is sent via SMS.
We reviewed some of Steven’s hacks and contributions over the years. Just go to the TADHack blog and search Goodwin to see his impact. Check out this piece Steven created on Engaging Developers (https://blog.tadsummit.com/2020/07/27/steven-goodwin-engaging-developers/). Make it easy for developers, use language the developer will understand, not industry insiders.
Over the years Steven’s advice has been adopted, and every sponsor that goes through TADHack comes out with a far better experience for developers.
Thank you Steven.
Remembering TADHack-mini Phoenix 2020, sponsored by Avaya with partners Google and GitHub.
Remembering TADHack-mini Phoenix 2020, sponsored by Avaya with partners Google and GitHub.
See all the winners here: https://blog.tadhack.com/2020/02/02/tadhack-mini-phoenix-2020-summary/.
We squeezed this event in just before the lockdowns began. 1-2 Feb 2020. I wasn’t worried about COVID going to this event. It was after Simcon 3, 5-6 March in the UK, that I realized all hell was breaking loose, when I got home I immediately bought a box of N95 face masks from Home Depot.
A big thank you to Phoenix developer and technology community for your support, including PHX DEVS LLC, #{az}devs, yesphx, Arizona State University, University of Advancing Technology (UAT) and many more.

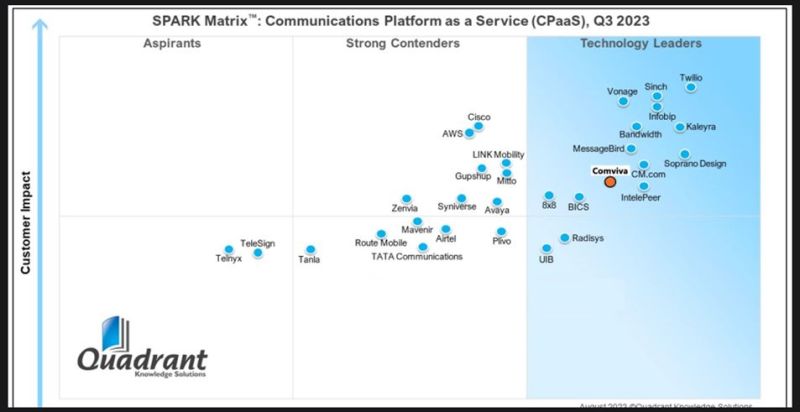
Truly Awful CPaaS Landscapes
I’ve written before about how CPaaS is a dumba$$ term. But what is truly awful are the competitive landscapes, utter nonsense is the word that comes to mind.
CPaaS is a handle Wall Street understands for being ‘Twilio-like’. Though Twilio was initially Programmable Communications, and is now CPaaSAI as Wall Street loves anything AI.
I just saw this landscape, see below, and it is bad. Though they did include UIB so props there. BICS bought Telesign as their CPaaS years ago, then bought another one, Route Mobile Limited and TeleSign are integrating under Proximus.
Telnyx is not bottom of the pile. Check out all the hacks developers built on Telnyx in 2021, https://blog.tadhack.com/2021/09/26/tadhack-global-2021-summary. I challenge all of the CPaaS in that landscape to achieve what Telnyx did. Where’s SignalWire, Commio? There’s another 30+ companies that should be included given the ones lists.
The category is programmable telecoms or communications if you prefer. The landscapes only make sense when you define the business segment / offer.
For example Mavenir and Radisys Corporation sell their platforms to carriers, who would then integrate with all their existing BOSS systems, relevant service platforms (e.g. SIP trunking), and negotiate A2P deals to deliver a comparable offer to say Twilio. That last point is what Carrier Relations managers do.
I recently read that Twilio is just a multiplexer of SMS. I am flabbergasted by the utter nonsense being presented at the moment, especially by those attempting to sell to telcos in the run up to MWC.
For over one decade, TADSummit and TADHack remain the only place you’ll get no BS, a big dose of Truth, and truly understand what is going on in Programmable Communications.
Juniper Research highlights $3B loss in SMS Business Messaging
The hit on A2P SMS is from multiple sources, not just IPMessaging like WhatsApp. As we pointed at TADSummit last year. Passkeys are having a major impact in SMS 2FA traffic across web brands and enterprise 2FA traffic.
Even email is substituting A2P SMS, it’s got that bad, see Twitter, given traffic pumping and AIT wrecking the web brands routing tables. And as we pointed out in the Augnet TADSummit innovators interview with Daniel Gill, opening up a new attack vector for ATO and other near real time fraud.
The US was a notable hold-out on SMS, however, the problems with The Campaign Registry and now with 800SMS are forcing enterprises to shift their technology choices as reliable delivery is critical, and now lacking in SMS.
The telco ecosystem is strangling the golden goose in an attempt to claim their “fair share”. While the A2P SMS ecosystem has ignored systematic issues as they were making good money, so everything is alright. This is a home grown problem, it did not need to be this way, inaction and greed will see several dramatic shifts in business messaging through ’24 and ’25.
US SEC set to require more transparency from SPACs
A little too late for many investors, but at least the SEC is finally addressing the SPAC problem.
The SEC began scrutinising SPACs after a gold rush of such deals in 2020 and 2021 sparked worries that target company financial projections were frequently wildly optimistic or misleading.
Gary Gensler, chairman of the U.S. Securities and Exchange Commission, said at the start of Wednesday’s meeting that the rules aimed to bring SPACs more closely in line with IPO rules. “Whether you are doing a traditional IPO or a Spac target IPO, Spac investors are no less deserving of our time-tested investor protections,” he said.
As a of last year, SPAC IPO value had fallen 98 per cent to just US$4 billion from a peak in 2021 while the performance of SPAC-launched stocks has tumbled more than 90 per cent, according to figures from Spac Research and the financial data firm Solactive.
SPACs have had a significant impact on some of the dysfunctionality in telecoms M&A.
Real-time HLR Scam
Ameed Jamous shared an incident that happened to a friend who landed in Dubai. This story sheds light on a serious scam targeting tourists and raises questions about data privacy. Likely this time hlr data is being sold in near real time to a third party who is executing the scam campaign.
The Incident:
Just an hour after arriving, my friend received a message, claiming to be from the General Directorate of Residency and Foreigners Affairs. It stated their information was incomplete and threatened a hefty fine.
The message included a link to update their details: [https://bit.ly/3vjseyc], which redirected to a fake site ([https://lnkd.in/d7zeEJi7], mimicking the legitimate https://gdrfad.gov.ae/en
The Consequence:
Unaware, his friend falls for it, entered their credit card details on the fake website, leading to financial risk and potential identity theft.
The solution is available:
1.Protect HLR Data: Customer HLR (Home Location Register) data is sensitive. It shouldn’t be sold or shared, especially not with third parties. This data indicates when someone arrives in a new country, and its misuse can lead to targeted scams.
2.Whitelist Sender IDs and Content: The recent scam used a pre-whitelisted sender ID, “GDRFA”, which allowed the scam message to pass through filters. Telcos should not only whitelist sender IDs but also scrutinize the content, including URLs, particularly for government entities. This ensures only legitimate information reaches the customers.
3.Integrate Free AI models: If implementing content whitelisting is challenging, consider using AI-based solutions like Open Text Shield (OTS). We’ve open-sourced OTS, which can integrate with any SMSC (Short Message Service Center), to dynamically block scam messages and protect users.
People, Gossip, and Frivolous Stuff
Given the GTC majority stake acquisition in Oofty, Guillaume Bourcy is now Partner & Chief Identity Officer at Global Telco Consult (GTC).
Konstantin Milekic is now Senior Strategic Account Executive at VOX SOLUTIONS.
Michelle Reese is now Co-Founder and CEO at PartneringAI
Daniel Soroko Donvito is now Contact Center Service Ops & Reliability Lead at BBVA IT España
You can sign up here to receive the CXTech News and Analysis by email or by my Substack.