The purpose of this CXTech Week 28 2024 newsletter is to highlight, with commentary, some of the news stories in CXTech this week. What is CXTech? The C stands for Connectivity, Communications, Collaboration, Conversation, Customer; X for Experience because that’s what matters; and Tech because the focus is enablers.
You can sign up here to receive the CXTech News and Analysis by email or by my Substack. Please forward this on if you think someone should join the list. And please let me know any CXTech news I should include.
Covered this week:
- Twilio’s Authy Incident
- Programmable Communications and Industry 4.0
- Refining the Voxist Whitepaper
- Congratulations to Kevin Britt on BT’s A2P SMS fraud reduction
- Vida Unveils AI Voice Agent Platform
- People, Gossip, and Frivolous Stuff
Twilio’s Authy Incident
Last weekend I was able to publish my research into Twilio’s Authy incident. A comment from acjy linked to the CCC (Chaos Computing Club), “CCC finally published some info too https://www.ccc.de/en/updates/2024/2fa-sms“
Background
As the Authy incident has propagated across the industry since the 1st July, I’ve received quite a few emails on this that corroborate the incident’s origins and the organizations involved. The Verge did a nice summary on the situation, with 33 million numbers exposes.
The ShinyHunters hackers announced on the relaunched BreachForums website in late June that they were leaking 33 million random phone numbers associated with Twilio’s two-factor authentication app Authy. Not only Chaos Computing Club (CCC), but also the hacker group ShinyHunters, a black-hat criminal hacker group that is believed to have formed in 2020 and is said to have been involved in data breaches against AT&T and Microsoft.
Details
The release of the customer data wasn’t Twilio directly, it was one of their partners, iBasis and their partner IdentifyMobile who exposed certain SMS-related data sent by iBasis publicly on the internet that included personal data. This included personal data and non-personal data (such as data related to marketing campaigns) was initially accessed by a security research group while it was publicly exposed by IdentifyMobile.
The immediate learning is Twilio needs to get into the guts of its partners. iBasis has been in / out of SMS. Some of the consultants iBasis used in the past I’d never do business with one in particular I consider a serial crook.
I’d assumed IdentifyMobile was no longer in business years ago as their website is dated 2015. Some of the 10 people on Linkedin associated with IdentifyMobile also work with other organizations. I’d assumed a zombie corporation, clearly I was wrong.
Twilio relies on numerous partners to maximize deliverability to their final destinations. Twilio was notified that iBasis had used IdentifyMobile who inadvertently enabled public access on an AWS S3 Bucket during development work.
Information contained in this bucket was made public from May 10-15, 2024, and accessed between May 13-14, 2024. Based on a joint investigation between IdentifyMobile and Amazon AWS, Twilio learned that a portion of this data was accessed by the Chaos Computing Club (CCC), and Black Hat hackers have also accessed the data. All the timings appear to line up.
CCC is a security research group that identifies security issues; CCC has confirmed that they are not holding any data downloaded from the AWS S3 Bucket. While Twilio continues collaborating with these companies to bring the most accurate information regarding this exposure, the portion of data exposed by IdentifyMobile related to SMS sent between January 1, 2024 and May 15, 2024, and included:
- Mobile number
- SMS message content
- SMS Sender ID
- SMS Timestamp
What has Twilio done so far?
Twilio initiated its incident response process to investigate this matter.
Twilio escalated this issue to the iBasis executive team; subsequently, they’ve done an analysis on the data logs that were compromised. Twilio has ceased sending traffic to iBasis where possible.
iBasis informed Twilio that it has stopped routing with IdentifyMobile.
Twilio will continue working with iBasis / IdentifyMobile to get any additional details that may arise from this incident.
Summary
There are too many layers in the messaging onion. iBasis was in, then out, then back in SMS. I’d assumed IdentifyMobile was no longer in business given the state of its website and the few people on Linkedin associated with the organization, that was wrong. iBasis were using them.
Public access on an AWS S3 Bucket during development work happens, I’ve seen it happen in the past, it’s rare. But the scale of this booboo is massive, 33 million.
Chaos Computer Club (CCC) is Europe’s largest association of hackers with 7,700 registered members. Founded in 1981, the association is incorporated as an eingetragener Verein in Germany, with local chapters (called Erfa-Kreise) in various cities in Germany and the surrounding countries, particularly where there are German-speaking communities.
Members of the CCC have demonstrated and publicized a number of important information security problems. The CCC frequently criticizes new legislation and products with weak information security which endanger citizen rights or the privacy of users. They’re good guys.
Someone made a mistake at IdentifyMobile, the good guys (CCC) caught it, but also the blackhats, this is typical. The complete development process must be reviewed, as well as the people who’ve advised them. Twilio needs to place security and compliance above price. I’d have questioned what services IdentifyMobile was providing for iBasis, as well as their development processes. I would have raised a concern on using iBasis in the first place given some of the people involved in the past 4 years and its lack of commitment to messaging.
As a postscript the CEO of Twilio on the 1st July sold 11,241 shares at $56.29. That timing is unfortunate given the ShinyHunters, a black-hat criminal hacker group, announcement in late June the Authy breach.
CCC’s Post
Two-factor authentication via SMS has been under attack for some time. Through techniques like SIM swapping or exploiting SS7 vulnerabilities in mobile networks, attackers can intercept SMS messages. Alternatively, users can be tricked through phishing attacks into revealing their one-time passwords. The CCC advised against using SMS as a second factor as early as 2013. Nonetheless, 2FA-SMS is widespread. It offers more security than simple password authentication. NIST.gov (National Institute of Standards and Technology) did this back in 2016. However, something is better than nothing, so SNS 2FA continues. However, fraud has driven customers away.
IdentifyMobile, a provider of 2FA-SMS, shared the sent one-time passwords in real-time on the internet. The CCC happened to be in the right place at the right time and accessed the data. It was sufficient to guess the subdomain “idmdatastore”. Besides SMS content, recipients’ phone numbers, sender names, and sometimes other account information were visible.
Over 200 companies that entrusted this provider directly or indirectly through other service providers with the security of their authentication were affected. This included companies like Google, Amazon, Facebook, Microsoft, as well as Telegram, Airbnb, FedEx, and DHL. Over 198 million SMS leaked in total.
By simply viewing the live feed, it would have been possible to:
- Take over WhatsApp numbers
- Conduct financial transactions or log in to various services without access to the phone, provided the password was known
To truly misuse the SMS codes, attackers would typically still need the password. However, “1-click login” links were also included in the data. For some large affected companies, only individual services were protected by IdentifyMobile. Nevertheless, IdentifyMobile’s negligence exposed companies and their customers to significant risk. This is evident from the numerous similar inquiries from data protection departments worldwide now reaching us through all channels.

Programmable Communications and Industry 4.0
Last week we published a podcast with Matthew Smith on his TADSummit presentation in October.
After this podcast a storm of conversation was stimulated across the Industry 4.0 community on Unified Name Space:
- Matthew D. Smith asks if Unified Name Space the ultimate system architecture? https://lnkd.in/dEsNDQT5
- https://lnkd.in/dQJa7su2 – from Enri Marini on the confusion around UNS (Unified Name Space)
TADSummit’s focus is the role of programmable communications in Industry 4.0, examples being vCon from Strolid, Inc. and Real Time Enterprise AI from Voxist – both were mentioned by Matthew D. Smith.
Programmable communications enables it to be an integrated part of Industry 4.0, rather than a black box labelled telecoms, that only the telecoms folks manage. We’ve never seen this level of integration before. It’s still early days, however, both Strolid, Inc. and Voxist have Industry 4.0 in their roadmaps.
We have several Industry 4.0 presentations planned for TADSummit 22-23 Oct. As always, for 12 years, TADSummit brings innovators together to set out the future of programmable communications.

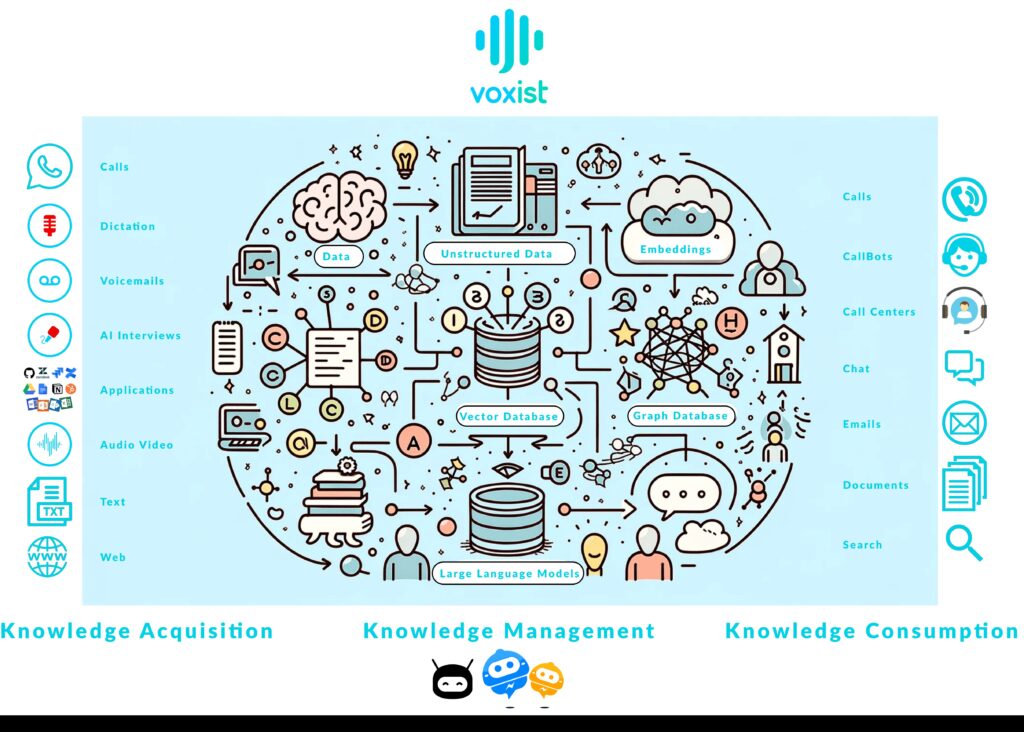
Refining the Voxist Whitepaper
Last week we did a Podcast on the Voxist white paper, a draft of was released to those who had time to review. We have some great feedback. Matthew Smith did a nice Linkedin post on the importance of Voxist to UNS (Unified Name Space).
Most operational comms meetings are not captured, and even if they are, the data capture is poor. Examples are meetings at the start and end of a production shift. Could be on the factory floor, a meeting room, break room, even online.
Other issues include: accents, limited writing abilities, vocabulary / acronyms, speaker identity, strong enough ASR, lack of computer availability.
Based on work Karel is doing with clients, those with mobile phones call into a bridge while they have an in person meeting. No fancy mic, just speak into the phone, and listen to everyone as normal. Covers multiple recordings, some speaker identification (based on corporate directory), improves ASR performance, mobile tends to work on the factory floor (indoors or outdoors). Strong accents with a phone line can receive additional processing to improve ASR.
Employee motivation is automatic summary, actions, notes, and feeds into UNS (Unified Name Space), think real time event driven architecture that captures the real-time state of the business. It’s a significant gap for most production lines today.
Karel gave examples of recording train announcements in stations and on trains, so the IT system has a better idea of train times and onboard bar status, e.g. bar open announcements and reminders, if they ran out of something. This led Matthew to highlight OEE (Overall Equipment Effectiveness), to be able to say, ‘blockage on blue line, stopping to reset and relaunch’. Rather than clicking on lots of menu options to confirm before stoppage.
Lots more feedback was gathered helping Karel refine the message, as well as realizing some contacts he can use to help drive new business around Voxist and Industry 4.0.
Congratulations to Kevin Britt on BT’s A2P SMS fraud reduction
A2P Messaging product manager for EE, Kevin Britt, revealed in a Linkedin post that starting from 10th July 2024, the operator will block all banking and logistics-based SMS unless it’s submitted via a single dedicated A2P Trusted bind.
The move will allow BT to implement more aggressive and robust blocking controls with the comfort of having no false positives.
Britt urged businesses to make sure they speak to their supplier to check they are prepared as a bespoke setup could be required.
He said that Commify, Infobip, Sinch, Stour Marine, Twilio, Vonage, and Webex CPaaS Solutions firms have confirmed they are ready for the change,
The move comes as Britt says BT has seen an 83% reduction in A2P SMS smishing on its network since March 2023.
Britt commended fellow BT employees and partners:
- law enforcement actions supported by colleagues dedicated to investigating and mitigating smishing;
- bespoke firewall developed by BT’s Messaging Operations team; and
- the SMS partners who comply with the Code of Conduct that BT introduced in September 2023.
Some of the key commitments in the anti-smishing code that BT introduced last year include:
- blocking messages where the Sender ID includes one of a series of words often exploited by scammers, such as ‘bank’, ‘caution’ and ‘package’;
- restricting who may use names associated with specific reputable organizations, such as ‘Mastercard’, ‘Student Loans Company’ or ‘Uber’;
- limiting the special characters permitted in a Sender ID to eliminate the risk of criminals using lookalike characters to mimic genuine organizations;
- blocking messages from numeric IDs that do not begin with a UK dial code;
- blocking short codes that do not follow permitted formats; and
- blocking suspected spam or fraudulent URLs included within the body of a message.
From my perspective the combination of picking the right partners, creating a traffic light warning system (openness in publishing who is on the naughty list to your partner ecosystem – and yes even some of those partners could be in the naughty list), adding liquidated clauses to agreements and implementing sender ID registry in combination provide critical protections around their firewall.
A firewall can be good or bad, depending on the situation. In the bad old days firewalls would come with revenue targets!! But I’ll not dive into that rat hole.
Kevin is, in my opinion, an impressive ‘poacher turned gamekeeper’. Creating a template for the industry, and the industry should celebrate this success.

Vida Unveils AI Voice Agent Platform
Lyle Pratt‘s new start-up is Vida. I’ve known Lyle since Bettervoice, and through Inteliquent / Voyant / Sinch. Vida has raised a $3 million seed funding round led by Los Angeles-based investment firm Stillmark Venture Capital.
Vida provides lifelike and realistic AI voice and messaging agents for SMBs, SMEs, Developers, and Individuals via its in-house proprietary platform. Answer calls and texts with AI that always works and is never busy. Its available as a service and through the Vida API.
Digerati Technologies, a San Antonio-based provider of UCaaS services to SMBs via its operating subsidiary Verve Cloud, has signed with Vida to incorporate its AI agents into is UCaaS offerings, said Digerati CEO Arthur Smith.
Digerati offers a complete bundle for small businesses when it comes to connectivity and UCaaS, with nearly 50,000 business users primarily across 4,300 to 4,400 customers in Texas, Florida and California.
We have a TADSummit Innovators Podcast with Lyle on 7th August to discuss Vida. He will also be presenting at TADSummit in October, 22-23.

People, Gossip, and Frivolous Stuff
Andy Woollard is joining Allsop Intelligent Software as VP Alliances & Partnerships. I’ve known Andy for over 15 years, since his time at BEA Systems.
Salvador Diaz joined the Black Hills Corp. (NYSE: BKH) team as director of investor relations.
Kevin Evans is now Senior Technical Specialist at Microsoft.
Jeroen de Rooij is now Senior Project Manager at Sound.
Michael Riemer is now Co-Founder and CEO at LoadLogic.
You can sign up here to receive the CXTech News and Analysis by email or by my Substack.